It's now official, account passwords for the popular business social network LinkedIn have been compromised.
Vicente Silveira, a director at LinkedIn, has confirmed that some of the passwords that were published online by a Russian hacking group "correspond to LinkedIn accounts". How many of the 161 million LinkedIn members have been impacted by this breach is as yet unknown, however it is likely to be a relatively small percentage as the published list of passwords is 'only' 6.5 million in number, even if LinkedIn passwords prove to be the vast majority if not all of them.
 The list of compromised passwords was published in a file that contained the passwords in unsalted SHA-1 hashed form, and appeared online in a Russian based public forum. I am led to believe that at least a quarter of a million of these hashes have been cracked, and that number will inevitably increase as the cracking work continues. Although no associated account data such as usernames were published within the file, at this point in time it is unknown if the hackers have access to this information or not.
The list of compromised passwords was published in a file that contained the passwords in unsalted SHA-1 hashed form, and appeared online in a Russian based public forum. I am led to believe that at least a quarter of a million of these hashes have been cracked, and that number will inevitably increase as the cracking work continues. Although no associated account data such as usernames were published within the file, at this point in time it is unknown if the hackers have access to this information or not.
Silveira admits that the password hashes were unsalted when he says "it is worth noting that the affected members who update their passwords and members whose passwords have not been compromised benefit from the enhanced security we just recently put in place, which includes hashing and salting of our current password databases".
It would appear that this exposed file has been put together as the result of a LinkedIn breach. Although this cannot be confirmed as of yet, the fact that LinkedIn appears in so many of the compromised passwords while no other social network name does (users often append numerical passwords with the name of the service it applies to, and LinkedIn has appeared many times so far in this list) leads me to believe this is a LinkedIn compromise.
If, as seems entirely possible, the hackers have username information then the business-centric nature of LinkedIn means that this could be a very serious compromise indeed. Stuart Coulson, cybersecurity expert and director of data centres at cloud specialist UKFast, warns that “This is really concerning for businesses as once hackers have usernames and passwords they can not only access the account, they can access any account with the same username and password. As many users have the same login details for LinkedIn, Facebook and even their work email, this hack has the potential to hand cybercriminals an open book of all of your personal, and potentially business, information.”
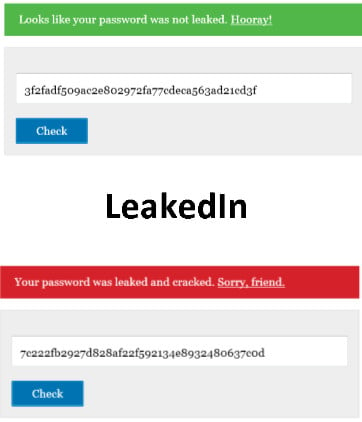
It's possible to run your own password through a SHA-1 hash generator and then compare this to the published file to see if it has been compromised. The easiest way to do this is to use a service such as LeakedIn which will do the hash generation and search for you. My 38 character randomised password was not leaked, however that has not stopped me from changing it immediately. I would advise all other LinkedIn users do the same. What's more, I would advise that they do so again once LinkedIn announces that whatever the security hole that allowed this compromise to take place was has been plugged. If your password was compromised or not, and you use the same password on mutliple sites, you should immediately change all your logins to use unique passwords.
