A cyber weapon grade piece of malware, some twenty times the size of Stuxnet, has apparently been fired at a number of countries in the Middle East. This highly complex piece of code which takes screenshots of any open 'programs of interest' such as email or IM, records audio and sends large volumes of compressed sensitive data back to base, was uncovered thanks to research from Kaspersky Lab and the International Telecommunication Union (ITU). Described as being far more functional and far more complex than previous nation-state sponsored attacks such as Stuxnet, Flame has been found to be actively deployed within Egypt, Iran, Israel, Lebanon, Saudi Arabia, Sudan and Syria so far.
 Perhaps the most surprising piece of information that has emerged about this cyber weapon is that it appears to have been first fired some two years ago in 2010. At present, however, there are no clues as to which nation-state is behind the worm. That is if it is, indeed, a state-sponsored attack at all. The chances do appear high that it is, given the complexity of the code and the fact that this isn't some bank login scraping affair or something that delivers a denial of service or site defacement payload. So if we rule out the organised cyber-criminal gangs and the political hacktivists, that only really leaves the nation states. It has been suggested that there are 'similarities' with Stuxnet in the code design itself, but at this moment in time whether this points to Flame and Stuxnet being weapons from the same cyber-armoury is open to much debate within the IT security industry.
Perhaps the most surprising piece of information that has emerged about this cyber weapon is that it appears to have been first fired some two years ago in 2010. At present, however, there are no clues as to which nation-state is behind the worm. That is if it is, indeed, a state-sponsored attack at all. The chances do appear high that it is, given the complexity of the code and the fact that this isn't some bank login scraping affair or something that delivers a denial of service or site defacement payload. So if we rule out the organised cyber-criminal gangs and the political hacktivists, that only really leaves the nation states. It has been suggested that there are 'similarities' with Stuxnet in the code design itself, but at this moment in time whether this points to Flame and Stuxnet being weapons from the same cyber-armoury is open to much debate within the IT security industry.
What is known for sure is that Flame has been very specifically targeted at particular computer systems within the countries where it has been found, rather than launched in a blunderbuss fashion.
Flame itself was discovered by accident, which makes it even more 'impressive' from a technical viewpoint. This worm has been active in the wild for two years, is a complex piece of code that makes Stuxnet look truly simplistic, yet has gone undetected until now. Researchers at Kaspersky Lab only stumbled across it while investigating a particularly destructive piece of malware known only as 'Codename Wiper' at this point in time, malware that was deleting data on computers in Western Asia. Wiper has still not been tracked down, but the researchers spotted another piece of unknown malware during their analysis of the attack logs, and this turned out to be Flame.
Eugene Kaspersky, CEO of Kaspersky Lab, says “the risk of cyber warfare has been one of the most serious topics in the field of information security for several years now. Stuxnet and Duqu belonged to a single chain of attacks, which raised cyberwar-related concerns worldwide. The Flame malware looks to be another phase in this war, and it’s important to understand that such cyber weapons can easily be used against any country.Unlike with conventional warfare, the more developed countries are actually the most vulnerable in this case.”
Kaspersky Lab’s experts are continuing to reverse engineer the multiple modules made up of several megabytes of executable code that comprise Flame in the hope to reveal more details of the threat, including possibly more clues as to the origin of this super cyber-weapon. At the moment though the answer to the who fired Flame question is unknown, and that may remain the case.
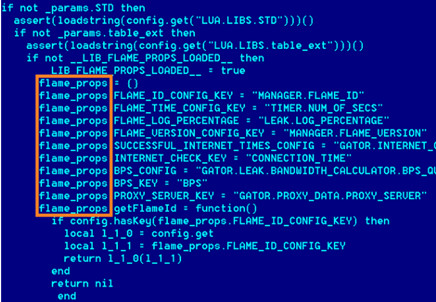
To find out more about Flame, including details of how the LUA scripting language, extended and interfaced with C code, has been used with many parts of the worm having high order logic written in LUA with effective attack subroutines and libraries compiled from C++ visit the Kaspersky Lab Flame FAQ.