It's been a year now since the Dyre malware family was first profiled, and there is no sign of infection rates slowing down. In fact, reports would seem to suggest just the opposite with infections up from 4,000 at the end of last year to 9,000 at the start of this. The lion's share being split pretty evenly between European and North American users.
So I was interested to spot this Tweet from Ronnie T @iHeartMalware who is actually Ronnie Tokazowski, a senior researcher at PhishMe, which declares: "I'm tired of dumping #Dyre configurations by hand. So I wrote a python script to do it. Enjoy folks!"
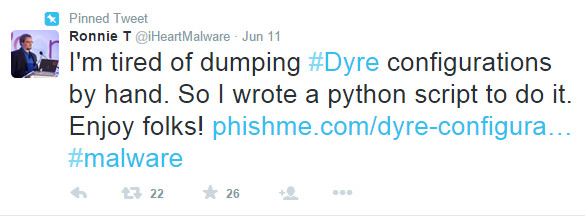
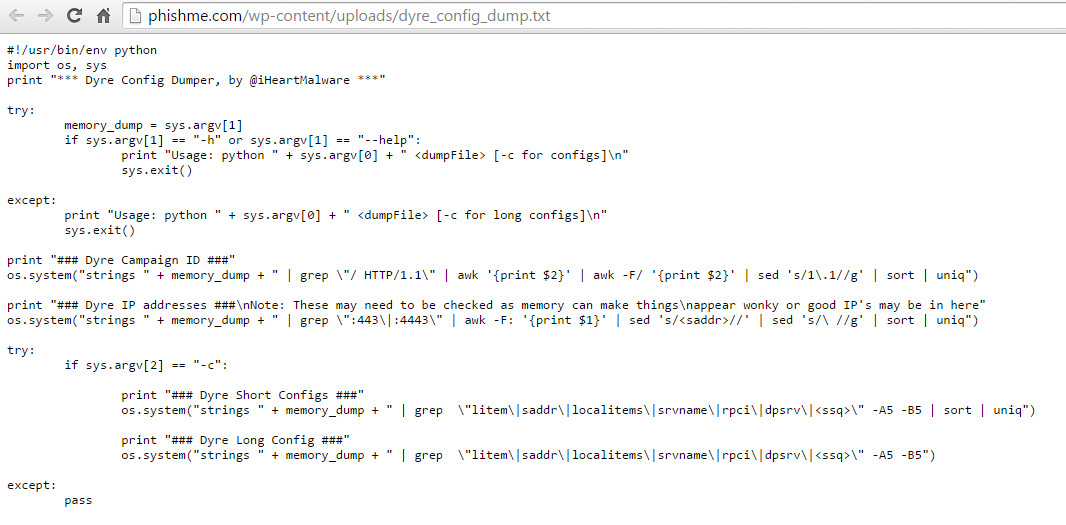
Ronnie explains "It’s been over a year since Dyre first appeared, and with a rise of infections in 2015, it doesn’t look like the attackers are stopping anytime soon. At PhishMe we’ve been hit with a number of Dyre attacks this week, so to make analysis a little easier, I tossed together a quick python script that folks can use for dumping the configurations for Dyre. To dump the memory, you can use Process Explorer to do a “full dump” on the process they inject into. (Typically the top-most svchost.exe, sometimes explorer.exe)."
Here's the script for all you Python fans to have a look at.