Malicious Virus attack!
Dear Forum members;
I am running Windows 7 Ultimate 64-bit. I contracted a dsc.exe virus yesterday. Solutions I found for removing it did not work – I assume they were written for other OS’s. However, this morning I managed to remove it using MBAM. I quarantined all the viruses, in case of problems, and problems have appeared:
1) There are strange messages on bootup:
On starting up, the system gives two Run DLL reports:
There was a problem starting
C:\Users\Xuyuan\AppData\Local\imanivago.dll
The specified module could not be found.
There was a problem starting
C :\Users\Xuyuan\AppData\Local\kSLexi.dll
The specified module could not be found.
2) Whenever I try to upload or send email, firefox crahes, forcing me to reboot the computer. This happens sending Gmail, and also uploading docs to this forum. It gives the following error, and I cannot access any programs without rebooting. I have unloaded and reinstalled Firefox once already, to no avail.
Microsoft Visual C++ Runtime Library
Runtime Error!
Program: C:\Program Files (86)\Mozilla Firefox\firefox.exe
This application has requested the Runtime to terminate it in an
unusual way.
Please contact the application support team for more information.
I thus don’t see the point in contacting Firefox, as the issue is with something that MBAM removed during the cleanup of dsc.exe.
As per forum instructions, I have already downloaded and run Microsoft® Windows® Malicious Software Removal Tool, which found nothing.
I ran ATF-Cleaner.
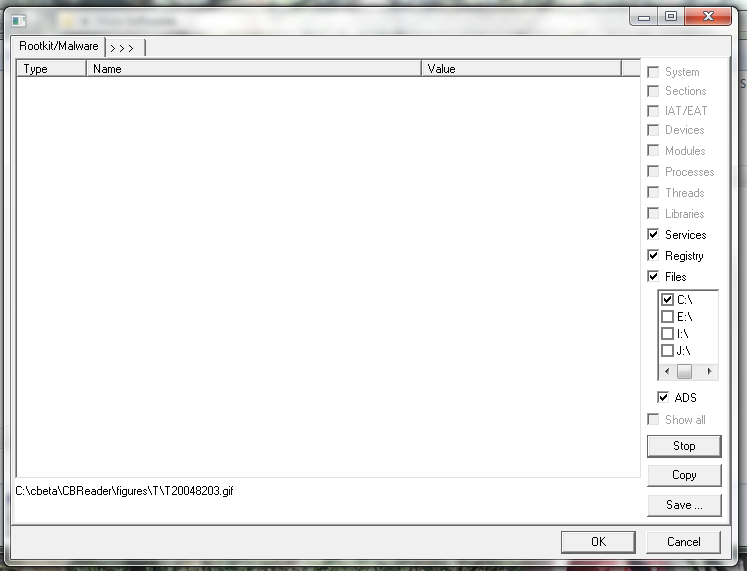
When running GMER Rootkit Scanner, it yielded the following message on startup:
C:\Windows\system32configsystem: The system cannot find the file specified.
And when it opened, most of the options were greyed out, apart from Services, Registry, Files and ADS.
On scanning it gave the following error message:
C:\Windows\system32\config\system: The process cannot access the file because it is being used by another process.
It then reported that it hadn’t found any system modification.
I then ran MBAM once again. With X result.
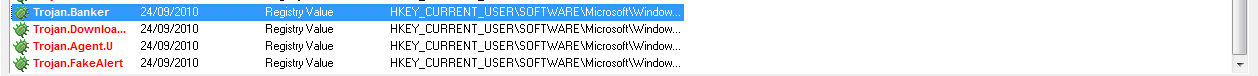
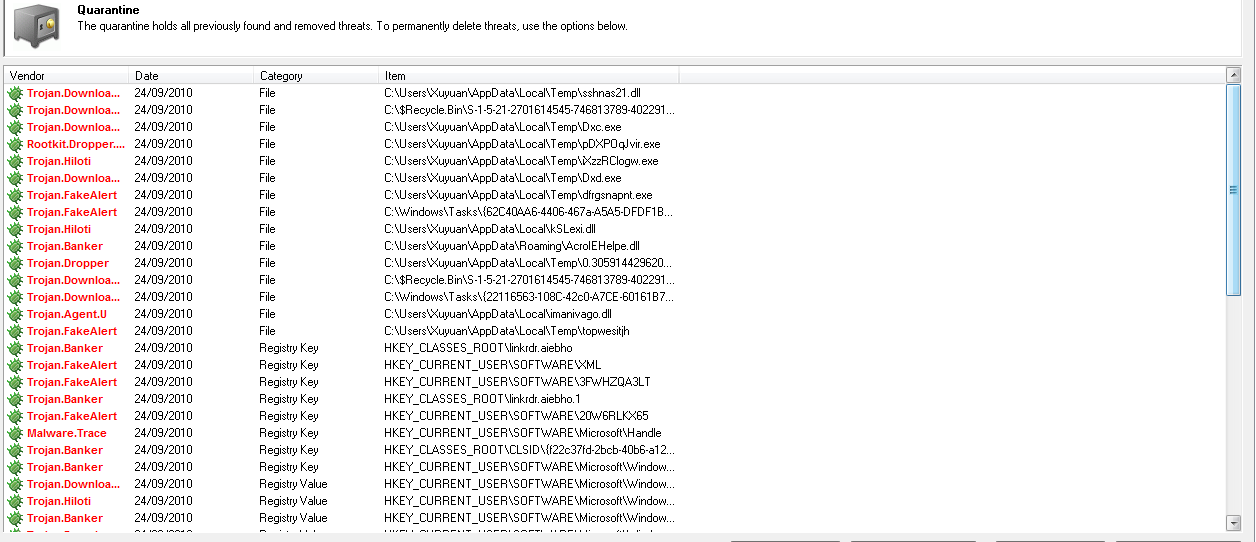
I’ve attached a picture of all the viruses MBAM picked up, some of which I think I need to clean or reinstall clean versions of to get my system running again, as well as a Hijack this log, and the two DDS scans.
Quite desperate, as Firefox, with all of its bookmarks and extensions, is imperative for my work!
Thanks so much for your help!~