I'm beginning to wonder... I hope someone can clarify my doubts.
First let me explain. So I've been using codeigniter's session library without much thought. I assumed the code was just some wrapper for PHP native sessions. So I assumed it was stored server side so encryption and all that jazz I needn't worry about.
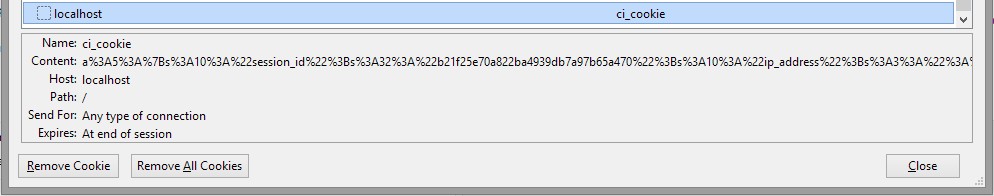
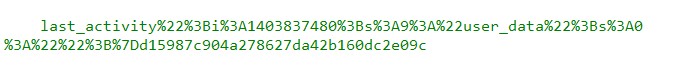
Then I began to do some digging and realised to my horror it is stored client side in the cookie. Codeigniter uses it's own session, it is not a PHP session at all.
Now I know you can't use codeigniter's session without setting an encryption key. So I assumed, great it must be encrypted by default- phew.
But get this... if you don't change the sessions config file to.
$config['sess_encrypt_cookie'] = TRUE; <--True
isn't it storing all your codeigniter sessions in plain text!!! So if I set a session isloggedin('yes') couldn't the user edit the cookie in plain text if I didn't set the sess_encrypt_cookie to TRUE. And more importantly isn't this the default codeigniter install setting?! It is set to false, so what's the point of forcing the user's to enter an encryption key before using codeigniter's sessions!?
Second I've been reading about countless issues with their session library logging people out when a site heavily relies on ajax. I'm assuming this might be one of the reasons DW had issues with users getting logged out from time to time.
I'm starting to think this is pretty lousy.
Well the session class at least. I don't know have I got the wrong end of the stick? Veedeo /Cereal/ Dani?