Anyone here had experience with PayPal Content Security Policy?
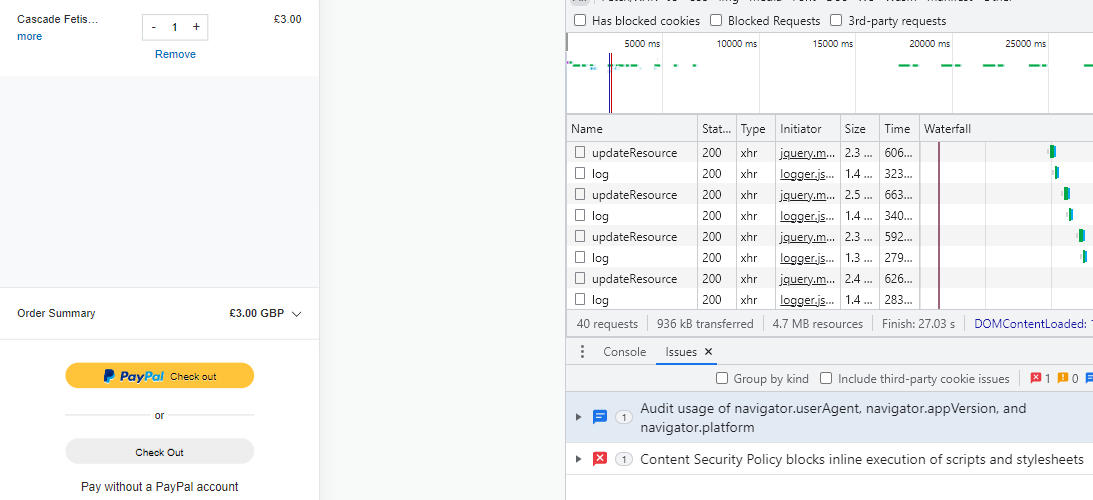
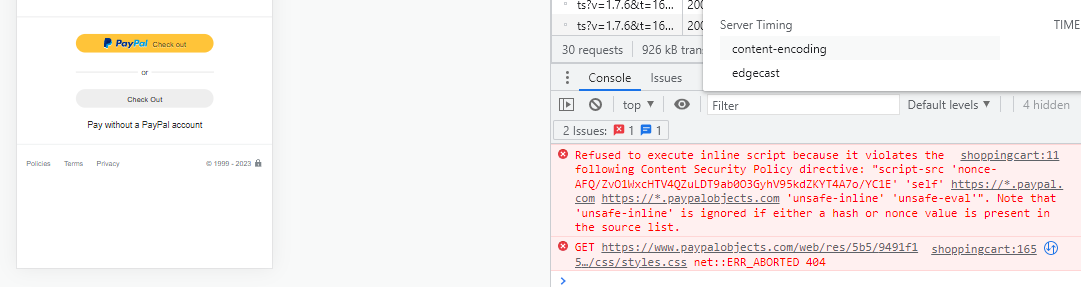
I tried to make a dummy purchase using Chrome Developer tools and this message is written in the bottom box: Content Security Policy blocks inline execution of scripts and stylesheets
(See attachment)
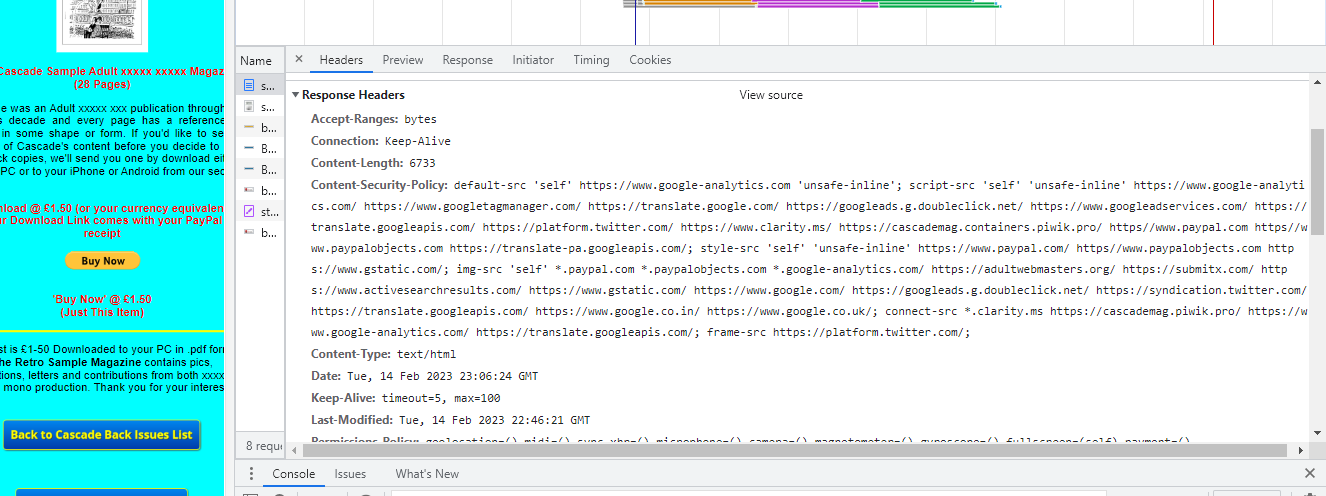
There must be a line of code to go in the <head> lurking somewhere, PayPal doesn't want to make it simple.
So, does anyone have any knowledge of this CSP? It's certainly preventing any PayPal sales that's for sure.