Chinese computer manufacturer Lenovo has admitted that it installed an adware component called Superfish on 16 million PCs shipped between September 2014 and February 2015 in order to "help customers potentially discover interesting products while shopping" according to an official statement made by the company. Although there is some argument to be had as to the validity of the 'helping customers' idea regarding software which injects third party adverts into Google searches and websites without the explicit permission or knowledge of the user, where there is no debate to be had at all is in the bloody great security hole Superfish drives through any Lenovo computer it is installed upon. It is true that Superfish doesn't, as far as I can tell, monitor user behaviour or record user data and instead uses contextual and image-based methods; meaning that users are not tracked as such. However, it is also true that it does some things which have the potential to be very dangerous indeed and that potential looks like it could soon become a very tangible reality.
The problem being twofold: firstly there's the not so small matter of Superfish having a pre-installed root CA certificate on your brand new Lenovo right out of the box. This enables it to intercept not just some websites that the user visits, but pretty much any of them and that includes HTTPS-protected ones, to inject adverts. Yes, you read that right, a trusted root certificate that you didn't know about and that allows adware which you also didn't know about to essentially perform a man-in-the-middle attack against your computer. This may sound like I'm being over excitable but stick with me for a moment. By dropping this self-signed certificate into the chain of trust, Lenovo is allowing Superfish to not only see your traffic but also alter it. Lenovo is allowing Superfish to act as the root certificate authority and therefore determine what encrypted communications are trustworthy. Think about it, this means that Superfish could generate encryption certificates that appear totally valid as far as the browser client is concerned for any HTTPS site such as, oh, Facebook or Google or your bank. If that's not a man-in-the-middle scenario then what is?
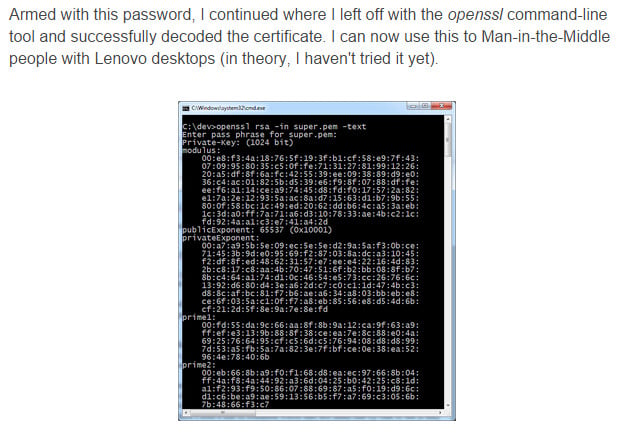
But it gets worse than that as we examine the second of the twofold huge security hole drivers I mentioned earlier. Let's imagine that someone managed to extract the private key used by Superfish to sign that root certificate, and used it to sign their own certificates in an actual malicious man-in-the-middle attack scenario. Now let's imagine that, in actual fact, the exact same private key is being used for every Lenovo computer with Superfish installed. One key to rule them all. Heck, let's stop imagining because this is all real, very real indeed. Not only is it the same key for all Lenovo, but security researchers have already extracted it and made it public online. Which means that non-imaginary bad guys could sit on the same Wi-Fi network in a coffee shop or hotel lobby and simply intercept all your encrypted and therefore supposedly private SSL connections.
Still, things couldn't get any worse could they? Well, yes, they could. While we wait for the first reported exploits of a Superfish man-in-the-middle attack to hit the headlines, those same media outlets (and Lenovo itself) are offering advice on how to remove the Superfish adware, or should that be badware? Which is good, right? Sort of, is the correct answer. User awareness of the issue is always a good thing, but not so great if they uninstall Superfish and think that's the problem solved. It won't be as the uninstall leaves the root certificate behind just sitting there waiting to be exploited.
The following Lenovo notebooks may be affected:
E-Series: E10-30
Flex-Series:
Flex2 14, Flex2 15
Flex2 14D, Flex2 15D
Flex2 14 (BTM), Flex2 15 (BTM)
Flex 10
G-Series:
G410
G510
G40-70, G40-30, G40-45
G50-70, G50-30, G50-45
M-Series:
Miix2 – 8
Miix2 – 10
Miix2 – 11
S-Series:
S310
S410
S415; S415 Touch
S20-30, S20-30 Touch
S40-70
U-Series:
U330P
U430P
U330Touch
U430Touch
U540Touch
Y-Series:
Y430P
Y40-70
Y50-70
Yoga-Series:
Yoga2-11BTM
Yoga2-11HSW
Yoga2-13
Yoga2Pro-13
Z-Series:
Z40-70
Z40-75
Z50-70
Z50-75
So what should you do, and advise family members, friends and work colleagues who own one of these Lenovo laptops to do?
Visit the LastPass Superfish Checker with your Lenovo laptop and keep your fingers crossed that you get the green tick fish showing your computer has not been impacted by the vulnerability.
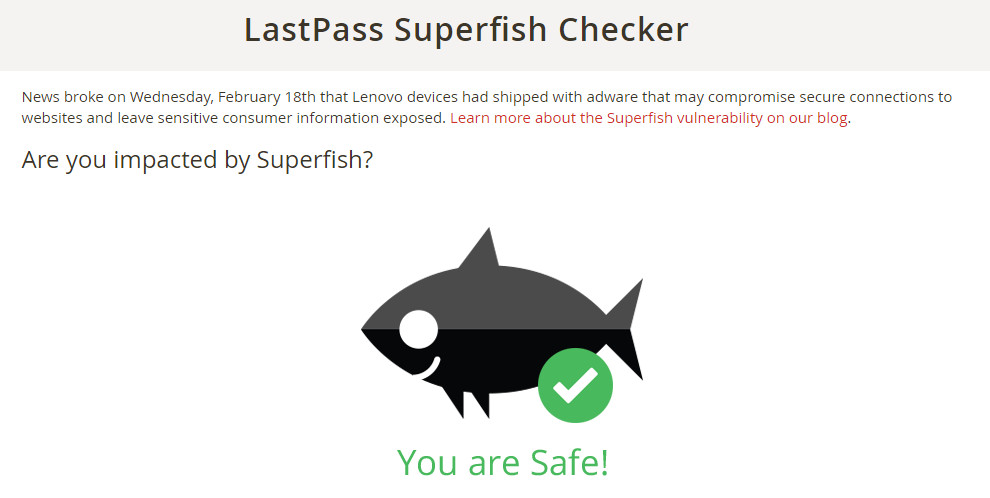
If the checker shows your Lenovo does have Superfish installed, then first go to your Windows Control Panel and uninstall 'Superfish Inc VisualDiscovery' in the usual way that you would uninstall any application.
Once that has been done, you need to get rid of the root certificate as well. Launch the Windows certmgr.msc application by typing 'certmgr.msc' into the Windows search box.
Click on the entry for 'Trusted Root Certification Authorities' and then 'Certificates' which will open a list of certificates for you to browse.
Right click and delete any certificates which mention Superfish Inc. Then restart your computer and re-run the Superfish Checker to make sure you've cleaned everything up and got that green tick.
