Research published today by data governance software developer Varonis reveals that, when it comes to the virtualized environment, security awareness appears to be something of a black hole.
The study found that data security in these virtualized environments can all too often be totally neglected, and some 48% of IT organisations reported or suspected there had been unauthorised access to files kept on virtual servers. The findings suggest that when it comes to awareness of security matters regarding virtualized servers and the data stored upon them, the harsh truth of the matter is that there is very little. Indeed, the survey found that 70% of those questioned had 'little or no' auditing in place for example.
When you consider that Gartner reckons there are now in excess of 50 million Virtual Machines installed on servers, it should come as no surprise to discover that 87% of respondents to the Varonis study said their application servers were already virtualized. The reasons for this virtualization being mainly a combination of deployment speed (76%) and disaster recovery potential (74%). Yet file security appears to be neglected almost across the board.
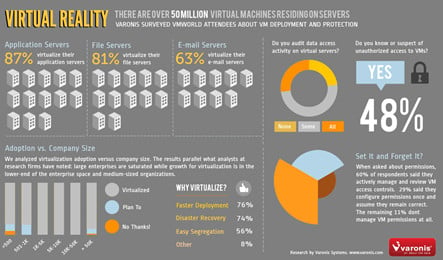
Sure, nearly 60% did claim to be "very careful about setting permissions and controlling subsequent updates" there's no escaping from the fact that 70% had implemented little or no auditing regardless of the company size. A statistic made all the more surprising by the revelation that in enterprises of more than 5,000 employees some 20% admitted to having "no file logging capabilities in place" at all.
Yet, against this backdrop of security ignorance, 48% had either reported or suspected that unauthorized access to files on those virtualized servers had taken place, putting sensitive company information at risk. Even when it comes to those companies that do audit their virtualized environments, a rather large 68% thought there had been unauthorized access.
"We suspect that for IT departments, virtualization may be something of a black box. We have found that, after a workload is virtualized, the actual details of managing file permissions and monitoring access is considered to be automatically ‘taken care of’. It is also quite possible that the teams managing virtualization projects see file security and governance as outside their discipline. The security team may have no visibility of what is happening”, said David Gibson, VP of Strategy at Varonis.
