11. How is my eFarewell Video Message unlocked after I have passed away?
Your eFarewell Video is Vaulted material which will be unlocked upon eFarewell’s confirmation of your passing based on verifying your PII with the Social Security Administration, your Death Certificate, and/or your Obituary.
slfisher 0 Posting Whiz
thanks! glad you liked it!
slfisher 0 Posting Whiz
Such as, not responding to the email I got this morning, purporting to be from Google, that I had to give it my account, date of birth, and password within 72 hours or my Google Mail account would be canceled, and "Google will not be heard responsible."
slfisher 0 Posting Whiz
I expect there's plenty of people out there who'd be willing to show them. :)
slfisher 0 Posting Whiz
Oh, here we go. It's just a week long in Australia.
http://www.staysmartonline.gov.au/news/news_articles/regular/national_cyber_security_week
slfisher 0 Posting Whiz
slfisher 0 Posting Whiz
Along with Vegetarian Awareness, Toilet Tank Repair, and Pet Wellness, October is National Cyber Security Awareness Month.
Who knew.
"The National Cyber Security Alliance, along with the U.S. Department of Homeland Security and the Multi-State Information Sharing and Analysis Center, sponsors National Cyber Security Awareness Month every October since its founding in 2003. The three organizations work together to help consumers, schools, businesses and government agencies stay safe online, with October being a special time for focused public awareness and education."
(Why October? They don't say.)
Simultaneous events will be held on Monday in Seattle and Arlington, Va., with speakers such as Howard Schmidt, Special Assistant to the President and Cybersecurity Coordinator for the White House, and Jane Holl Lute, Deputy Secretary for the U.S. Department of Homeland Security.
In addition, an October 6 event at Intel headquarters in Silcon Valley will offer on online safety awareness and education hosted by the National Cyber Security Alliance and the Anti-Phishing Working Group, including a “Smokey Bear” national public awareness campaign on cybersecurity.
(You think I'm making this stuff up?)
Have your own event planned? Register it.
slfisher 0 Posting Whiz
The state of Oregon is holding a series of informational meetings in 20 areas around the state to identify the barriers to bringing Internet resources to their community.
While obviously meetings are being held in urban locations such as Portland and the state capital of Salem, they are also being held in rural and remote locations such as John Day and Madras (with 5,078 residents, according to the 2000 census).
The meetings are part of a project funded by the American Recovery and Reinvestment Act of 2009, also known as the stimulus package. Oregon received a $1.6 million Broadband Data Collection and Mapping Grant and a $498,610 Broadband Planning Grant to conduct Internet initiatives in the state and support efforts to develop and ensure the implementation of state broadband strategies.
Work is being led by a company called One Economy under contract with the Public Utility Commission of Oregon (PUC), and in collaboration with the Oregon Business Development Department, and the Oregon Broadband Advisory Council. The groups are administering a public survey to assess Internet use and its demand, and will report the availability, affordability, and adoption of broadband technology within Oregon.
Oregon residents can also respond to the survey online, which contains demographic information as well as what barriers people are encountering, such as "It is not available where I live," "I can’t afford it," "I don’t like to sign contracts," issues with credit scores, or not having enough knowledge about what …
slfisher 0 Posting Whiz
According to a new study from the Pew Internet & American Life Project, 21 percent of American adults do not use the Internet. And of those, 90 percent say they have no intention of using the Internet in the future.
Among the non-internet users, 34 percent do have some relationship with the online world, ranging from living in a home with an Internet connection or having used the Internet at some point in the past.
As far as reasons, 48 percent say they are too busy or not interested, while 21 percent are concerned about the price and 18 percent cite usability concerns, such as that it is too difficult or they don't know how. Surprisingly, only 6 percent said they didn't have Internet access.
These statistics are down slightly from a similar study Pew did in January, 2009. In that study, 25 percent of adults weren't on the Internet at all and were unlikely to change, with 33 percent of them not being interested and 13 percent of them not having access.
In general, however, the statistics are not greatly changed from the 2009 study, Pew said. The one major exception is in African-Americans, where the broadband-adoption gap between blacks and whites has been cut nearly in half. (A survey earlier this year found a big jump in interest in the Latino population.)
Interestingly, the survey went on to ask users about government efforts to expand …
slfisher 0 Posting Whiz
It's not unusual for a government IT department to warn its users about downloading malware onto their government-issued computers. It's more unusual, though, for the source of the malware to be the ads on the website of the newspaper of record.
In July, the cyber security coordinators in the state of Idaho took the unusual step of recommending that its users block or avoid the website of the Idaho Statesman, a Boise-based daily paper that covers most of the state, due to what was said to be malware in the website's ads, according to a memo sent to the security team.
Upon presumably reporting the problem to the paper, the paper began scanning the ads for malware before placing them on the site, and the state IT department also looked for malware in the paper's ads.
"Therefore, since there are many agencies or individual employees who must access the Idaho Statesman, their business needs must be met; particularly since the overall risk seems to have returned to a normal, cautious state. I no longer recommend blocking or avoiding the Idaho Statesman website, though anyone who does should be cautious," the memo continued, which alluded to a similar incident in January as well. (Boise State University, which is funded by the state, reported a similar incident in December, 2009.)
"The Statesman is not alone in having issues with malware; many local and national news sites (including the New York Times and the Seattle …
slfisher 0 Posting Whiz
"It's unbelievable, the kind of data that's out there about you," Cisco's principal security strategist Patrick Gray told a crowd in Boise, Idaho, this morning.
The problem is that criminal hackers can use that kind of information to target a company, Gray said. He described one case where criminals in the Ukraine targeted a particular large company, went onto Facebook to look for employees of that company, and upon finding one, created a Facebook account in the name of one of her high-school friends and asked to "friend" her. When she did so, the "friend" then suggested she click on a link to see a picture of herself from high school -- which downloaded malicious software into the corporation's network, he said.
Before joining Cisco, Gray spent 20 years with the Federal Bureau of Investigation, including forming one of the first cybercrime units.
In particular, Facebook is huge, Gray said, noting that if it were a country, it would be the third-largest worldwide, after China and India. In other Facebook statistics:
- 50 percent of active Facebook users log on to Facebook on any given day
- 60 million users update their status daily
- People spend more than 500 billion minutes per month on Facebook
- 3 billion photos are uploaded every month
- 5 billion pieces of content are shared each week
- Millions of local businesses have pages
- More than 20 million people become fans of pages
- There is a total of 5.3 billion fans
- 100 million people use …
slfisher 0 Posting Whiz
There's a map for that.
And now nonprofits can get it for free.
ESRI, the company that produces the ARCView series of geographic information systems applications, announced today its Nonprofit Organization Program, intended to provide copies of the seminal mapping software for free to nonprofits.
"The Esri Nonprofit Organization Program is designed to provide conservation and humanitarian nonprofit organizations around the world an affordable means of acquiring ArcGIS software and services," the company said. Other types of nonprofit organizations may also be eligible for membership in the program.
Mapping software is an extremely useful way of displaying data with a geographic component. For example, in making the announcement, ESRI demonstrated finding connections between maps of rates of poverty, obesity, and diabetes -- important public health issues.
Free software includes not only the base package, but also extensions, such as ones that support remote sensing applications, which are useful for global issues such as climate change and pollution. Nonprofits can get up to 750 seats and 20 servers running the software.
Typically, the software is very expensive, in the thousand-dollar range.
The announcement was made at the Gov 2.0 Summit, held in Washington, D.C. this week.
slfisher 0 Posting Whiz
A number of civil liberties groups announced today that they are fighting U.S. Department of Homeland Security policies that allow them to search all electronic devices -- including laptops, cameras, and smart phones -- that cross the border.
Between October 1, 2008 and June 2, 2010, more than 6,500 people -- nearly 3,000 of them U.S. citizens -- were subjected to a search of their electronic devices as they crossed U.S. borders, reported the groups, which include the National Association of Criminal Defense Lawyers (NACDL), the American Civil Liberties Union (ACLU), and the New York Civil Liberties Union (NYCLU).
This is an issue for criminal defense lawyers because some of the people who had their equipment searched were criminal defense attorneys, who believe that the searches violate attorney-client privilege.
“The policies allow border agents to detain the devices even after a traveler has been permitted to enter the country so that they can continue their searches. The policies do not place any time limits on how long DHS can keep travelers’ devices, nor do they limit the scope of private information that may be searched, copied or detained,” according to the complaint.
In addition, while these searches are nominally only for border crossings, in practical terms they can cover a much broader area. "Border Patrol agents operating across the nation claim the authority to question Americans about their immigration status anywhere within 100 miles of the border," wrote Udi Ofer, …
slfisher 0 Posting Whiz
yes, that's my take on it as well. 1. It's unlikely that it's technologically possible. 2. If they wanted to, no bill or law would stop them.
slfisher 0 Posting Whiz
Well, I'm not going to make the argument that Prostitution is Good. My point, which you also made, is that many other sites are publishing such ads as well, and Craigslist made a lot of effort to get information about the people placing the ads. The ads won't stop, they'll just be more difficult to track down.
slfisher 0 Posting Whiz
I don't know about that aspect :) but I agree that Craigslist is being unfairly targeted.
slfisher 0 Posting Whiz
Yeah, that would be interesting, if Russia or China were to bomb *us* for what it perceived as hacking coming from the U.S.
slfisher 0 Posting Whiz
Nations such as Russia and China who have malicious hackers should be held accountable for the actions of those criminals, according to a report from the Council on Foreign Relations, an independent, nonpartisan membership organization.
"Though the United States cannot expect countries to prevent all malicious behavior, it can expect them to secure their networks to a reasonable standard, pass laws outlawing international cyber crime, and have mechanisms in place to act on requests for assistance in shutting down attacks, and investigating and prosecuting them," wrote author Robert Knake. He is the coauthor, with Richard Clarke, of the book Cyber War.
In addition, the U.S. needs to lead by example, Knake said. "It should take steps to clean up its national network, work to stop its systems from being used in international cyberattacks, prioritize criminal investigation of cyberattacks with foreign victims, and make clear that the primary goal of its military efforts in cyberspace is to defend the United States and preserve international connectivity."
Steps the U.S. should take include developing a stronger set of international regimes to fight crime in cyberspace, moving beyond the current Council of Europe Convention to draw in non-Western states, and developing realtime mechanisms for collaborating to stop cyberattacks in progress and investigate attacks across borders; developing new norms and pursuing treaties to protect the core functions of the Internet and ban distributed denial-of-service attacks; and updating the Internet's underlying technologies to be more secure, …
slfisher 0 Posting Whiz
LiveJournal users are up in arms over a modification to the service that they say allows users commenting to their online journals to also post those comments on Facebook or Twitter, even if the journal is set up to be restricted only to the owners' friends.
In response to the uproar, LiveJournal posted to its blog "Update: Thank you for taking the time to offer your honest feedback. We understand and appreciate your desire for privacy. We share your concerns. Most of us would not want to publish our LiveJournal usernames or FO comments to Facebook or Twitter either (to the extent we even use them). Please give us a little time to address your concerns. We are listening, and we'll do our best to respond."
As LiveJournal describes the new feature, "If you set your default to cross-post comments, ALL of your comments, including screened and Friends Only comments, can be cross-posted whenever you choose," though users must manually choose to cross-post the comment if is marked Friends Only or screened comment. "Of course, you can override your settings on a per-comment basis, so you have complete control over whether to cross-post each and every comment," the blog continues.
In other words, if one set up a LiveJournal to talk about activities that one wished to remain private, and set it up so that only one's friends could read it, then a friend commenting on one's private activities could choose to post the comment …
slfisher 0 Posting Whiz
Yes, there's definitely some decent companies out there.
slfisher 0 Posting Whiz
A lovely juxtaposition of two articles at TechCrunch this weekend: One expressed concern about discrimination against older workers in the computer industry; the other said that if women weren't successful in the tech industry, it wasn't men's fault.
(H/T to @jmhodges, whose Twitter posting provided inspiration for the title.)
The age piece, by Vivek Wadhwa, criticized the computer industry for discrimination against older workers, and offered older workers advice.
"My advice to managers is to consider the value of the experience that the techies bring," Wadhwa wrote. "With age frequently come wisdom and abilities to follow direction, mentor, and lead. Older workers also tend to be more pragmatic and loyal, and to know the importance of being team players. And ego and arrogance usually fade with age. During my tech days, I hired several programmers who were over 50. They were the steadiest performers and stayed with me through the most difficult times."
One could imagine a companion piece with a very similar tone, talking about the value of hiring women. However, that TechCrunch piece was very different.
"Success in Silicon Valley, most would agree, is more merit driven than almost any other place in the world," wrote Michael Arrington. "It doesn’t matter how old you are, what sex you are, what politics you support or what color you are. If your idea rocks and you can execute, you can change the world and/or get really, stinking rich."
Arrington is …
slfisher 0 Posting Whiz
Not only is there a debate about the constitutionality of using Global Positioning System units to help fight crime – now there’s concern about using Google Earth as well.
The Associated Press reported a few days ago that government officials in regions ranging from the Riverhead, N.Y., to the country of Greece are using Google Earth and other satellite imagery sites to locate items such as swimming pools without the proper regulatory permits or that indicate undeclared wealth.
The Chicago building department also uses it to look for pools, porches, and decks without the proper permits, while other Illinois cities use it as a reference to ensure that they’re inspecting the right building, the article continued.
It’s not the first time Google Earth has been used for this purpose; law enforcement officials have used satellite imagery, and then more readily available sites such as Google Earth, for some time to look for marijuana fields, with a telltale spectral signature, or buildings with more heat than they should have.
And as long ago as 2006, a Racine County, Ark., sheriff took the coordinates in a GPS unit owned by someone busted for pot, plugged them into Google Earth, and then executed searches in those areas, finding a number of marijuana growing operations.
(On the other side of the law, there has also been concern that Google Earth could be used by pedophiles to find parks and …
slfisher 0 Posting Whiz
I love the idea of depending on karma and the universe to get back at people, and in the meantime it's good to know what things I can do to prevent it. :)
slfisher 0 Posting Whiz
Geolocation features in cameras are giving thieves new information when someone proudly posts a picture of their new acquisition, whether it's a boat, a flat-screen TV, or a new car, according to an article last week in the New York Times.
Some cameras and smart phones embed location-specific information, such as latitude and longitude, into the metadata, or information, about a picture. Canny thieves can click on the picture, check the metadata, and determine the location of the prize, or just the house or garage full of power tools behind it. Combined with information such as posts about a user’s plans, like “Going on vacation next week with my new boat!,” it provides a to-do list for burglars.
While the geotagging feature can be disabled, it can be complicated, says the Times. “Disabling the geotag function generally involves going through several layers of menus until you find the “location” setting, then selecting “off” or “don’t allow,” the article said. “But doing this can sometimes turn off all GPS capabilities, including mapping, so it can get complicated.”
Browser plugins could enable burglars to use latitude and longitude to plot locations on a Google map. “By downloading free browser plug-ins like the Exif Viewer for Firefox or Opanda IExif for Internet Explorer, anyone can pinpoint the location where the photo was taken and create a Google map,” the Times said.
In fact, burglars with some technical savvy could even search for geotagged photographs accompanied …
slfisher 0 Posting Whiz
oh, good point, I hadn't even thought of the public transit aspect.
slfisher 0 Posting Whiz
The Maine State Bureau of Consumer Credit Protection reported today that it has received a query from an unnamed out-of-state finance company about placing Global Positioning System units into vehicles it finances or that its customers used as collateral, according to an article in the Bangor Daily News.
Such GPSes were not intended to help the company repossess the vehicle more easily or to track it in case of theft, but to ensure that the person was working by analyzing the person's traffic pattern, said bureau of consumer credit protection superintendent Will Lund, according to the article.
Worse, Lund said he could not find any authority of his office to block the use of such devices. Maine Attorney General Janet Mills also expressed concern that, once collected, the data could be used in other ways.
Privacy issues are increasingly a concern with GPS units and automobiles, according to an article yesterday in the New York Times. Particularly at issue is whether police attaching a GPS unit to a car under suspicion violates the Fourth Amendment law against unreasonable search and seizure, with different appellate courts issuing different rulings on its legality.
The Electronic Frontier Foundation and the American Civil Liberties Union also filed a brief in the most recent case, which "argued that unsupervised use of such tactics would open the door for police to abuse their power and continuously track anyone's physical location for any reason, without ever having …
slfisher 0 Posting Whiz
An Internet Service Provider (ISP) has finally been given permission to reveal that he was the recipient of an National Security Letter (NSL) from the Federal Bureau of Investigation (FBI) six years ago, demanding information about his clients.
Nicholas Merrill, president of the New York ISP Calyx, still can’t say on what specific date in February, 2004, he received the letter, nor the target of it from among his more than 200 clients, but he is now able to talk about the lawsuit that the American Civil Liberties Union (ACLU) filed on his behalf. He told Democracy Now! – incidentally, one of his clients – that his other clients included “household names” such as Ikea, Snapple Iced Tea, and Mitsubishi Motors, as well as nonprofit and nongovernmental organizations such as the New York Civil Liberties Union.
The letter requested that Merrill provide 16 categories of "electronic communication transactional records," including e-mail address, account number and billing information, plus several other categories redacted by the FBI, according to an article in the Washington Post.
"National security letters are a little-known FBI tool originally used in foreign intelligence surveillance to obtain phone, financial, and electronic records without court approval,” reported Mother Jones. “Rarely employed until 2001, they exploded in number after the Patriot Act drastically eased restrictions on their use, allowing NSLs to be served by FBI agents on anyone -- whether or not they were the subject of a criminal investigation. In …
slfisher 0 Posting Whiz
I knew Bill Gates was a Harvard dropout but hadn't realized Mark Zuckerberg was as well.
slfisher 0 Posting Whiz
heh! I'd never heard that story. Do you have a cite for that? I'm not finding it in a Google search of the Newsweek site.
slfisher 0 Posting Whiz
After two years of criticism against the online classified ad site Craigslist because people post ads for prostitution there, the site is now being accused of hosting ads for child prostitution as well.
"Last month, two girls trafficked for sex through the website Craigslist wrote an open letter to its founder, Craig Newmark, pleading with him to get rid of the adult services section, where sex ads are placed," wrote Malika Saada Saar, founder and executive director of the Rebecca Project for Human Rights, in CNN Opinion last week. The piece was purportedly written due to insufficient response from the Craigslist organization to the July letter.
The organization has now placed ads in newspapers such as the San Francisco Chronicle and the Washington Post, repeating the allegations, as well as placing the information on its website.
The letter, and the ad, claim to be from two girls, "A.K." and "M.C.," who report what they say is their history of having been sold on Craigslist.
What the organization wants is for Craigslist to shut down its Adult Services section, which Craigslist set up in November, 2008, in response to criticism by 40 state Attorneys General of its Erotic Services section. The Adult Services section requires a credit card verification, as well as a $10 charge. Craigslist is reportedly earning as much as $36 million per year from these charges.
The Craigslist organization, however, contends that it …
slfisher 0 Posting Whiz
You've been able to use the Internet to swap books, CDs, and DVDs. Now -- kids' clothes?
ThredUP offers a standard form factor for exchanging kids' clothes -- a UPS flat-rate box, packed full of clothes for a girl or a boy, of a certain size, for a certain season, and the clothes can either be tops, bottoms, or mixed. People select a box, pay $13 to have it shipped to them, then pack one of their own and list it for selection by someone else. (The company makes $1.50 on each box.)
But this isn't just an easy way to avoid going to garage sales. ThredUP was named one of five Boston-based startups to watch by Techland earlier this week, and received $1.4 million from four early-stage investors, including Founder Collective of Cambridge and New York, Trinity Ventures of Menlo Park, Calif., High Line Venture Partners and Nextview Ventures, according to Mass High Tech, which also reported this week that the company was moving from Cambridge, Mass., to California.
The site launched in April and now has 15,000 users, with 1,000 new ones signing up each week, reported the Associated Press. Thus far, it has shipped 3,000 boxes of clothes and has 1,500 listed, according to the Boston Globe. Initially, it was set up for adults, but shifted its focus to kids. It was also featured …
slfisher 0 Posting Whiz
A blogger for liberal sites such as AlterNet and News Junkie Post has reported discovering a conservative group of online users who systematically work together to bury, or vote down, stories on liberal subjects and by posters they believe to be liberal, in order to keep those stories from becoming more widely known.
"A group of nearly one hundred conservatives have banded together on a Yahoo Group called Digg Patriots (DP), and a companion site at coRanks to issue bury orders and discuss strategies to censor Digg and other social media websites," reported the blogger, known as oleoleolson, who is the Senior News Editor and Chief New Media Strategist for News Junkie Post. "DP was founded on 21 May 2009. Since then, over 40,000 posts have been logged at a steady rate of around 3000-4000 per month. The “Patriots” Network on coRank is a tool to submit Diggs to a group list as opposed to sending an e-mail every time. It also has some tools that make submitting to the list as easy as clicking on a bookmark."
The group -- which has since been deleted from Yahoo! -- also discussed strategy on how to either come back after being banned for life from Digg for violating the rules, set up sleeper profiles, and how to use multiple accounts at once without getting caught, which is against the Digg rules of one account per user, oleoleolson reported. Many of the primary posters …
slfisher 0 Posting Whiz
Google said on Wednesday that it was killing its Wave collaborative development environment, citing lack of interest, according to published reports such as in the Wall Street Journal.
Blog entries from Google appeared as recently as July 27; in fact, the Google Wave blog does not yet have any information about the shutdown, which was announced on the main Google blog.
"Wave has not seen the user adoption we would have liked," wrote Urs Hölzle, Senior Vice President, Operations & Google Fellow. "We don’t plan to continue developing Wave as a standalone product, but we will maintain the site at least through the end of the year and extend the technology for use in other Google projects. The central parts of the code, as well as the protocols that have driven many of Wave’s innovations, like drag-and-drop and character-by-character live typing, are already available as open source, so customers and partners can continue the innovation we began. In addition, we will work on tools so that users can easily “liberate” their content from Wave."
Google Wave was intended to be a web application for real-time communication and collaboration, Google had described the application. "People can communicate and work together with richly formatted text, photos, videos, maps, and more. Any participant can reply anywhere in the message, edit the content and add participants at any point in the process. Then playback lets anyone rewind the wave to see who said …
slfisher 0 Posting Whiz
oh, hi, Clayton! I'm really sorry you're having to deal with this.
Thanks for providing that legal stuff -- can you explain it in littler words? :)
slfisher 0 Posting Whiz
Good point!
slfisher 0 Posting Whiz
How many users do you have? In other words, how many individuals have recorded such messages?
slfisher 0 Posting Whiz
I'm not sure it's the only solution; the article I did a few months back, cited in the piece, listed a number of such services.
It's definitely a tough problem to solve without the risk of mistakes.
slfisher 0 Posting Whiz
The troubled newspaper industry has been railing for years about how the Internet is destroying their business model, and taking actions such as paywalls and talking about changing copyright law.
Now, one newspaper is going further -- it's taking bloggers that posted its stories to court, with the result that a number of blogs have been shut down and are facing multi-thousand-dollar settlement charges.

TheLas Vegas Review-Journal set up an agreement with Righthaven LLC that enables Righthaven to sue, on behalf of the Review-Journal, bloggers who reposted content from the paper. And it has done so, filing nearly 80 cases, regardless of whether the blog was commercial or gave credit to the source.
While some have claimed Righthaven has a right-wing agenda and is focusing on liberal blogs, conservative blogs have also been targeted.
"Righthaven has offered no prior contact, cease-and-desist warnings or any attempt at good-faith resolution whatsoever," reported The Armed Citizen , which posted six articles from the Las Vegas paper among 4,700 articles it has posted on the subject of Second Amendment rights. "The Armed Citizen has been excerpting articles from newspaper, TV station, and radio station websites for a number of years without a single complaint or infringement notice."
(Joe Strupp, of Media Matters, notes that, thus far, conservative Nevada political candidates who have posted entire articles have not yet been targeted, raising …
slfisher 0 Posting Whiz
If you're a woman, it'll tick you off.
If you're a man, hopefully it'll educate you.
It's "My Fault I'm Female," or " MFIF " for short, a compendium of everyday horror stories from women about how they've been treated on the job, by public servants, and by their family.
It's also the fastest-growing WordPress blog, as of earlier this month -- and it's only been around for eight days.
"MFIF (My fault, I'm female) is a blog that shares stories of women who've been made to feel it's their fault that they are female at work, at home, or wherever," the site describes. The site, which thus far primarily features stories from the U.K., is already receiving up to 30,000 hits per day.
It's also available on Facebook and Twitter (#MFIF hashtag).
Warning: NSFW.
slfisher 0 Posting Whiz
The issue of death and how to deal with it has already come to social media, with a number of social media sites having policies on how to deal with dead members, notifying the dead person's friends, allowing people to memorialize the dead, and so on.
But a new problem has been cropping up. With Facebook adding reminders to people to get in touch with their friends, it's inevitable that people have been getting some of these from beyond the grave, so to speak.
It happened to me last summer; a few days after a friend died tragically in a car accident, I got a Facebook message, chirping at me that I should "Reconnect with him!" Sigh. I wish I could.
"Facebook says it has been grappling with how to handle the ghosts in its machine but acknowledges that it has not found a good solution," reported the New York Times. "“It’s a very sensitive topic,” said Meredith Chin, a company spokeswoman, “and, of course, seeing deceased friends pop up can be painful.” Given the site’s size, “and people passing away every day, we’re never going to be perfect at catching it,”" she told the paper.
Because Facebook had started out being for college students, death hadn't typically been a problem, but it's going to be more likely, the Times said. "People over 65 are adopting Facebook at a faster pace than any other age group, with 6.5 million signing up in …
slfisher 0 Posting Whiz
A lot of people have tried a lot of things and gotten a lot of interesting results. :) I wish I could have described them all. Thanks for passing that on.
slfisher 0 Posting Whiz
In what way?
slfisher 0 Posting Whiz
A New Zealand company is reporting that its Twitter account has been suspended due to “Updates consisting mainly of links, and not personal updates" -- which, if true, means that any other business that posts a lot of links could suffer the same fate.
"I suspect the Reuters account http://twitter.com/reuters will be suspended very soon as clearly 99% of their posts are links back to their site," noted the social media marketing company, Business Blogs, tongue-in-cheek, in describing the situation. "Of course its not just Reuters – all profiles controlled by news agencies should be suspended as well."
The company found that its account had been suspended on July 15. "The Twitter profile took our staff over 6 months to build up to a 5,000 follower count by updating the profile with content at least 3 times per day," the company wrote . "There was no selling, no spam and no abuse."
What the company did do -- like many other companies -- was to use a third-party social media company, CampaignHub , to automate the posting of items to sites such as Twitter, Facebook, and LinkedIn, as well as to hold contests and promotions. And in response to Twitter spammers that make a business out of promising to build up one's Twitter following, the company has been cracking down on automated postings.
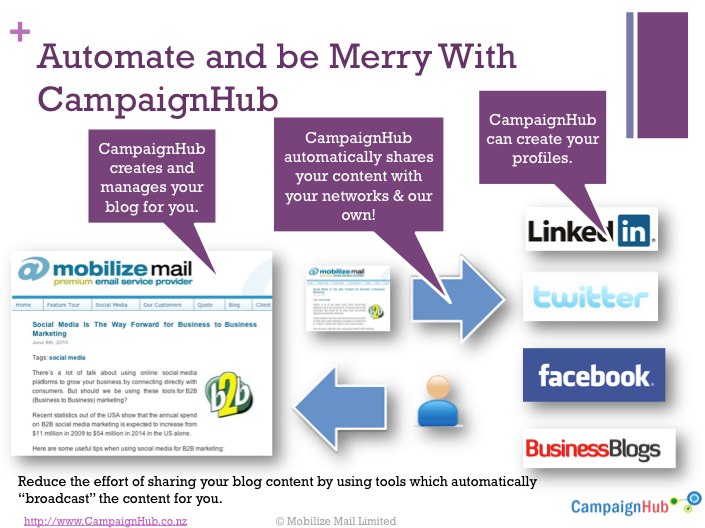
"Automated or mass-created affiliate advertising …
slfisher 0 Posting Whiz
Not that there's anything wrong with that. (cf. Seinfeld)
slfisher 0 Posting Whiz
A two-day marathon of almost real-time, personalized ads based on social media requests was so successful that it was causing Internet outages, according to an article on the campaign in AdWeek.
The 'Old Spice Guy,' actor Isaiah Mustafa, made more than 200 little videos over the course of two days from a studio in Portland -- in a campaign that has not only revitalized the Old Spice brand but which is likely to change the relationship between social media and advertising ongoing. “It just gives you a glimpse of where the world is going,” said Patrick Pichette, CFO of Google -- which owns YouTube, where the ads had their own channel -- during the company's earnings call. "In less than three days, the 65 response videos drew more than 5.2 million views on YouTube," and the brand’s Twitter followers grew to 48,000, from 3,000, reported the New York Times.
 The effort involved a team of writers, art directors, producers, editors and social media strategists, Adweek described. "The social media experts initially identified a crop of popular bloggers in key areas like entertainment (Perez Hilton), technology (4chan) and advertising (Adweek's own AdFreak), as well as regular YouTube and Facebook commenters. The social media team scours the Web for comments related to the Old Spice campaign. They feed ones that are funny or from interesting sources to the creatives, who then determine which make good fodder for humorous videos."
The effort involved a team of writers, art directors, producers, editors and social media strategists, Adweek described. "The social media experts initially identified a crop of popular bloggers in key areas like entertainment (Perez Hilton), technology (4chan) and advertising (Adweek's own AdFreak), as well as regular YouTube and Facebook commenters. The social media team scours the Web for comments related to the Old Spice campaign. They feed ones that are funny or from interesting sources to the creatives, who then determine which make good fodder for humorous videos."
Videos included …
slfisher 0 Posting Whiz
I write like Dan Brown.
At least, that's according to the I Write Like site , which was sweeping the Intertubes yesterday (more than 100,000 hits in a single day) as people tried to find out which Famous Writer their deathless prose most resembled. (Brown is the critically slammed author of The DaVinci Code.)

The site was put up on July 9 by Coding Robots, a Silicon Valley-based developer, according to the company's blog .
"Currently it analyzes vocabulary (use of words), number of words, commas, and semicolons in sentences, number of sentences with quotation marks and dashes (direct speech)," wrote Dmitry, who claimed authorship.
The site has received some criticisms, with some people wondering whether it's a scam or simply a random result. People who entered text of Famous Writers into the site often found the text attributed to some other Famous Writer -- including, most notably, Famous Writer Margaret Atwood, who found her work most resembled that of Stephen King. "According to the I Write Like analysis, I write like... Ta da! Stephen King! http://bit.ly/bBCMB3 Who knew?" she tweeted .
"“The Raven” is written in the style of William Shakespeare. Shakespeare’s Sonnet 18 is written in the style of Charles Dickens. The first paragraph of Great Expectations is written in the style of P.G. Wodehouse. It seems authors never write in their own styles," commented one …
slfisher 0 Posting Whiz
"The children now love luxury; they have bad manners, contempt for
authority; they show disrespect for elders and love chatter in place
of exercise. Children are now tyrants, not the servants of their
households. They no longer rise when elders enter the room. They
contradict their parents, chatter before company, gobble up dainties
at the table, cross their legs, and tyrannize their teachers.
ATTRIBUTION: Attributed to SOCRATES by Plato, according to William L.
Patty and Louise S. Johnson, Personality and Adjustment, p. 277
(1953)."
Even though Socrates likely didn't say that, the sentiment is the same: Older people love to predict what they think kids are going to be doing with their lives.
Last week's Pew Internet and American Life Project report on "millennials" is no exception. "Millennials" are people born 1980 or later, meaning people who are now 30 or later. They've grown up with the Internet and social networking, and Pew wanted to know how they'll act as they age.
However -- perhaps thinking of the Marshall McLuhan quote, "I don't know who discovered water, but I'm pretty sure it wasn't a fish" -- instead of talking to a bunch of millennials, Pew talked to a bunch of old people.
Granted, these were special old people, experts in their field, some of whom had been on the Internet longer than Millenials have been alive: Clay Shirky, Esther Dyson, Doc Searls, Nicholas Carr, …
slfisher 0 Posting Whiz
slfisher 0 Posting Whiz
So there is. Thanks!
slfisher 0 Posting Whiz
What do children's book author Beatrix Potter, painter Mary Cassatt, and artist Frida Kahlo have in common?
According to one blogger, they are the three women -- compared with 109 men -- who have been honored by having a Google logo designed for them that is used on the worldwide Google page.
"With all that feminists need to focus on achieving for women in the world – equal pay for equal rights, bodily autonomy, political representation at all levels, actual recognition of women’s humanity – why waste time on who gets a little drawing on Google?" asks Shelby Knox. "Because we’ve lived with the myth that men created the world and everything good in it for long enough. As long as men get to designate who and what in history is important, young women will continue to learn that all their sex has contributed throughout all of history is their wombs."
Google is particularly important because of how often it is used by students, Knox goes on to say.
The specialty Google logos are called Google Doodles, and Google explains their history. There is also a canonical list of Google Doodles.
Commenters to the blog suggested a number of other women scientists, world leaders, and artists whom they felt Google should consider honoring.
Women aren't alone in feeling slighted; some people, including Barry Popik (who, ironically, is a college classmate of mine) criticize Google for not …

