According to a new study from the Pew Internet & American Life Project, 21 percent of American adults do not use the Internet. And of those, 90 percent say they have no intention of using the Internet in the future.
Among the non-internet users, 34 percent do have some relationship with the online world, ranging from living in a home with an Internet connection or having used the Internet at some point in the past.
As far as reasons, 48 percent say they are too busy or not interested, while 21 percent are concerned about the price and 18 percent cite usability concerns, such as that it is too difficult or they don't know how. Surprisingly, only 6 percent said they didn't have Internet access.
These statistics are down slightly from a similar study Pew did in January, 2009. In that study, 25 percent of adults weren't on the Internet at all and were unlikely to change, with 33 percent of them not being interested and 13 percent of them not having access.
In general, however, the statistics are not greatly changed from the 2009 study, Pew said. The one major exception is in African-Americans, where the broadband-adoption gap between blacks and whites has been cut nearly in half. (A survey earlier this year found a big jump in interest in the Latino population.)
Interestingly, the survey went on to ask users about government efforts to expand …

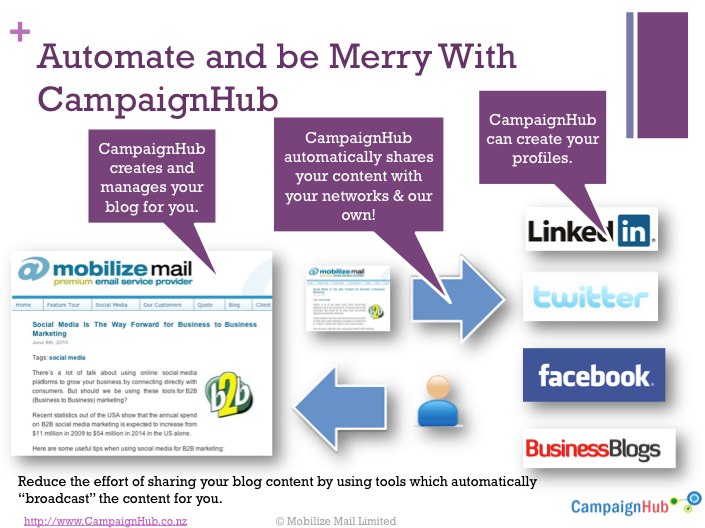
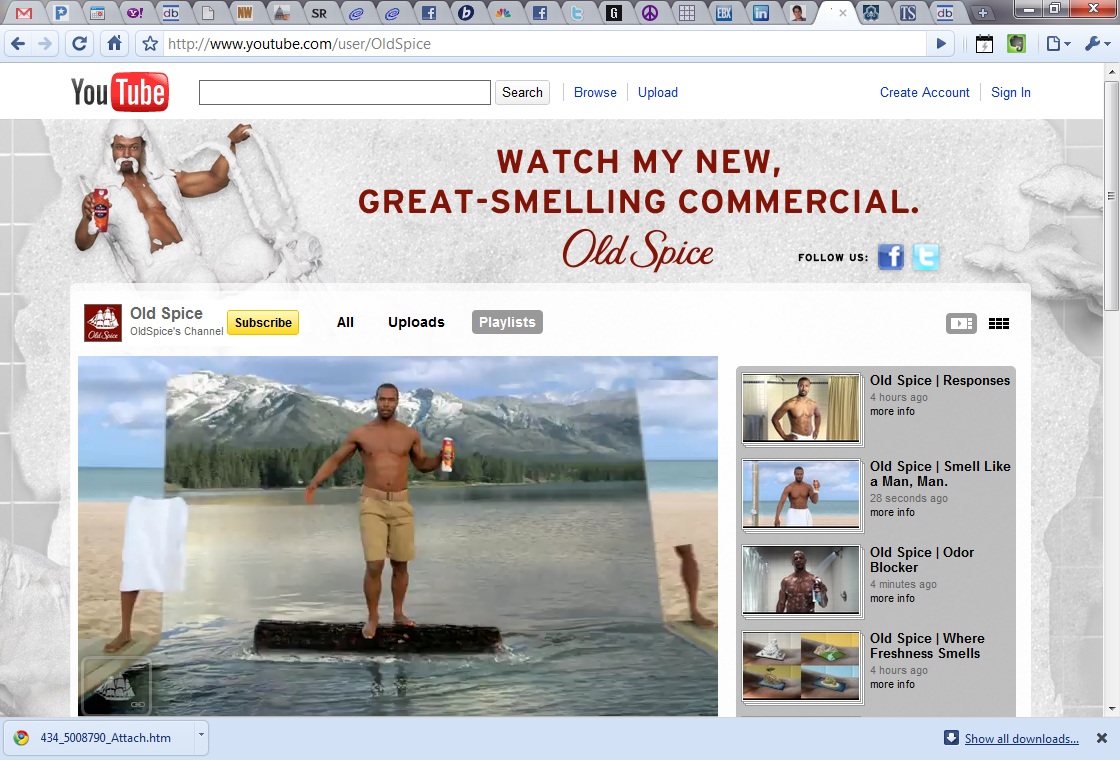 The effort involved a team of writers, art directors, producers, editors and social media strategists, Adweek described. "The social media experts initially identified a crop of popular bloggers in key areas like entertainment (Perez Hilton), technology (4chan) and advertising (Adweek's own AdFreak), as well as regular YouTube and Facebook commenters. The social media team scours the Web for comments related to the Old Spice campaign. They feed ones that are funny or from interesting sources to the creatives, who then determine which make good fodder for humorous videos."
The effort involved a team of writers, art directors, producers, editors and social media strategists, Adweek described. "The social media experts initially identified a crop of popular bloggers in key areas like entertainment (Perez Hilton), technology (4chan) and advertising (Adweek's own AdFreak), as well as regular YouTube and Facebook commenters. The social media team scours the Web for comments related to the Old Spice campaign. They feed ones that are funny or from interesting sources to the creatives, who then determine which make good fodder for humorous videos."