According to recent reports the Android operating system has an impressive 19.9% share of the US mobile web market. That's still some way behind Apple iOS on 58.8% but the iPhone has been around for a lot longer. It should come as no surprise, then, that Yahoo! wants to get a piece of that Android action. Which is why it has now announced the continuing expansion of its reach with the immediate availability of Yahoo! Mail and Yahoo! Messenger apps plus a Yahoo! Search Widget for Android.
 The new apps come complete with new functionality and enhancements that have been optimised for the Android platform, and are available for OS 2.0 or later from the Android Market as free downloads with immediate effect.
The new apps come complete with new functionality and enhancements that have been optimised for the Android platform, and are available for OS 2.0 or later from the Android Market as free downloads with immediate effect.
The new Yahoo! Mail Android app enables push notification of new messages, full search of email messages, photos uploading direct from the handset camera or gallery, emoticon and rich text formatting support. Importantly for Yahoo!, it also offers advertisers an opportunity to reach a highly engaged mobile audience and Samsung is the first and inaugural advertiser to take advantage of this. The new Yahoo! Messenger Android app enables sending of instant messages via SMS text message, multitasking with the app working and active in the background, push notifications, plus the same photo and rich formatting support as the Mail app.
The Yahoo! Android search widget is essentially just a one-click route to Yahoo! search, accessible from …

 Quite apart from the fact that it is nothing short of remarkable for an IT company to be hitting a 75 year milestone anniversary, and without wishing to sound too much like the new Fujitsu marketing manager, this is a birthday worth celebrating thanks to a number of breakthroughs and innovations which most of us have either forgotten about or were never aware of in the first place. From the early days of telephone switching in the 1930s; the mainframe and parallel computing generation of the 1970s, to newer inventions such as palm vein authentication and perhaps most recently the world's first 3D PC, Fujitsu are one of the unsung heroes of the technology business.
Quite apart from the fact that it is nothing short of remarkable for an IT company to be hitting a 75 year milestone anniversary, and without wishing to sound too much like the new Fujitsu marketing manager, this is a birthday worth celebrating thanks to a number of breakthroughs and innovations which most of us have either forgotten about or were never aware of in the first place. From the early days of telephone switching in the 1930s; the mainframe and parallel computing generation of the 1970s, to newer inventions such as palm vein authentication and perhaps most recently the world's first 3D PC, Fujitsu are one of the unsung heroes of the technology business. So after
So after 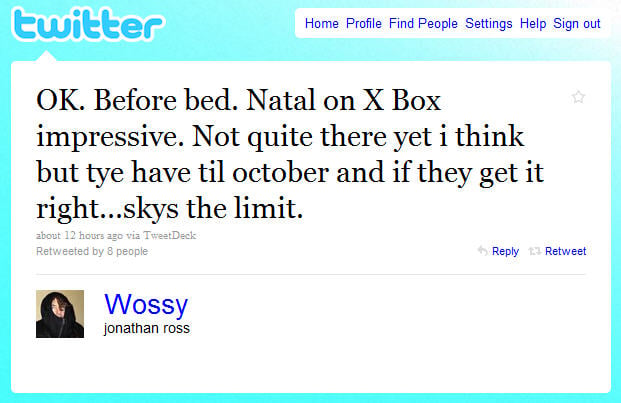 TV presenter and Twitter hero Jonathan Ross was amongst the glitterati of the gaming, gadget and entertainment industries who were invited to a 'top secret' hands-on briefing about Project Natal, hosted by Microsoft in London yesterday evening. He took his son with him, and his son posted a video of Ross playing with the new Xbox 360 Wii-alike controller to YouTube. If you want to see both in action, you can do so
TV presenter and Twitter hero Jonathan Ross was amongst the glitterati of the gaming, gadget and entertainment industries who were invited to a 'top secret' hands-on briefing about Project Natal, hosted by Microsoft in London yesterday evening. He took his son with him, and his son posted a video of Ross playing with the new Xbox 360 Wii-alike controller to YouTube. If you want to see both in action, you can do so